Archive for the 'Policy' Category
Monday, April 15th, 2013 by Bradley Huffaker
[While getting our feet wet with D3 (what a wonderful tool!), we finally tried this analysis tidbit that’s been on our list for a while.]
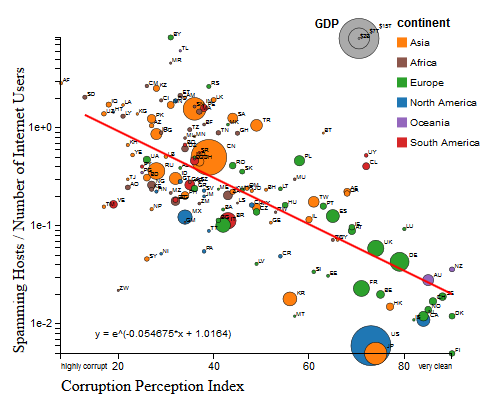
We recently analyzed the reputation of a country’s Internet (IPv4) addresses by examining the number of blacklisted IPv4 addresses that geolocate to a given country. We compared this indicator with two qualitative measures of each country’s governance. We hypothesized that countries with more transparent, democratic governmental institutions would harbor a smaller fraction of misbehaving (blacklisted) hosts. The available data confirms this hypothesis. A similar correlation exists between perceived corruption and fraction of blacklisted IP addresses.
For more details of data sources and analysis, see:
http://www.caida.org/research/policy/country-level-ip-reputation/
|
 |
 |
 |
x:Corruption Perceptions Index
y:IP population % |
x:Democracy Index
y:IP population % |
x:Democracy Index
y:IP infection % |
Interactive graph and analysis on the CAIDA website
Posted in Commentaries, Economics, Policy, Security, Visualization | 1 Comment »
Monday, March 5th, 2012 by kc
As part of our NSF-funded network research project on modeling Internet interconnection dynamics, we hosted the second Workshop on Internet Economics (WIE2011) last December 1-2. The goal of the workshop was to bring together network technology and policy researchers with providers of commercial Internet facilities and services (network operators) to further explore the common objective of framing an agenda for the emerging but empirically stunted field of Internet infrastructure economics. The final report (http://www.caida.org/publications/papers/2012/wie11_report/) attempts to capture the content, structure, and depth of the discussions, and presents relevant open research questions identified by workshop participants. From the intro (but the 5-page pdf is worth reading):
(more…)
Posted in Commentaries, Economics, Policy | No Comments »
Tuesday, February 7th, 2012 by Josh Polterock
Finally, a process we started almost three years ago has reached a milestone: the first public draft of The Menlo Report: Ethical Principles Guiding Information and Communication Technology Research and its Companion Report were posted on the DHS and SRI web sites (respectively) last month.
DHS’s Science and Technology Directorate, through its PREDICT program, sponsored this report on ethics in Information and Communication Technology Research (ICTR). The culmination of a multi-year effort by network and security research stakeholders to lay out a guiding framework to identify, navigate, and resolve ethical issues in ICTR, this report is intended to be a dialogue launch point for the community of researchers, oversight entities, and policymakers to reflect on ethical issues in security and network research. Public comments are encouraged via the Federal Register through 27 February 2012. I’m pretty sure all comments are responded to and/or integrated into the next version of this report. Hopefully the report will also be the topic of discussion at some conferences and workshops this year, so that the community can get out ahead of these issues before we find ourselves facing legislative overreaction to catastrophe (or even perceived catastrophe). Please consider reading and submitting a comment.
Posted in Commentaries, Policy | No Comments »
Friday, January 20th, 2012 by kc
I ended 2011 with a short (20 December) visit to a pleasantly warm Washington, D.C. for my 5th FCC Technical Advisory Council meeting. Some of the discussions from the third meeting were extended, others cut off for lack of time. We spent over an hour on the suggestion made by the Legacy Transition working group two meetings ago to advise the FCC to move forward in sunsetting (although we shunned that term at this meeting — “It’s a new beginning, not an end!”) the public-switched telephone network (PSTN). Many questions have arisen repeatedly in the discussions over the course of the last two meetings (and two FCC workshops in between), notably, “What happens to the telephony numbering system?” The initial strategy was imprecise, “The numbering plan will continue to exist but governance and allocation process needs to be considered.” Another repeated question has been “What exactly do we mean by PSTN?”
(more…)
Posted in Commentaries, Policy, Topology | No Comments »
Friday, August 26th, 2011 by kc
Policy making has become predominated by sponsored research, politics, campaign contributions and rhetoric. In light of an apparent disinterest for the facts it comes as no surprise that the network neutrality debate highlights opposing perceptions about the impact from changes in the next generation Internet. Regrettably no unbiased fact finding appears readily available, because politicization at the FCC prevents fair minded assessment by the Democratic and Republican Commissioners and heretofore the conflict has not generated a question of law or fact reviewable by a court.
— Rob Frieden: Internet 3.0: Identifying Problems and Solutions to the Network Neutrality Debate, 2007.
in June I participated on a panel on network neutrality hosted at the June cybersecurity meeting of the DHS/SRI Infosec Technology Transition Council (ITTC), where “experts and leaders from the government, private, financial, IT, venture capitalist, and academia and science sectors come together to address the problem of identity theft and related criminal activity on the Internet.” Here is a belated recap of my thoughts on that panel, including what network neutrality has to do with cybersecurity.
(more…)
Posted in Commentaries, Economics, Policy | 1 Comment »
Tuesday, August 23rd, 2011 by kc
[I posted the following on CircleID today:]
As is well known to most CircleID readers — but importantly, not to most other Internet users — in March 2011, ICANN knowingly and purposefully embraced an unprecedented policy that will encourage filtering, blocking, and/or redirecting entire virtual neighborhoods, i.e., “top-level domains” (TLDs). Specifically, ICANN approved the creation of the “.XXX” suffix, intended for pornography websites. Although the owner of the new .XXX TLD deems a designated virtual enclave for morally controversial material to be socially beneficial for the Internet, this claim obfuscates the dangers such a policy creates under the hood.
(more…)
Posted in Commentaries, Domain Name System (DNS), Economics, Policy | No Comments »
Monday, July 25th, 2011 by kc
My third FCC Technical Advisory Council meeting (3-hr. video archive here) was the most exciting yet. The TAC’s Critical Legacy Transition working group, studying the legacy public switched telephone network, recommended that the Council advise the FCC to set a concrete date to sunset (shut down) the Public Switched Telephone Network (PSTN). (!) The working group recommended the year 2018 as a starting point for lively discussion.
(more…)
Posted in Commentaries, Economics, IPv6, Policy, Review | 2 Comments »
Friday, July 15th, 2011 by Amogh Dhamdhere
Although the outcome is not good news, it is gratifying to see the predictions of a model of the Internet ecosystem being validated by the real world. Specifically, the recent spate of ISP consolidations is precisely what our network formation model predicts. First, Level3 acquired Global Crossing in a deal valued at $3B. A few months later, Centurylink (QWEST) acquired Savvis for $2.5B. Our model predicts that this consolidation will continue unless ailing tier-1 providers find a new source of revenue to compensate for their losses on IP transit.
(more…)
Posted in Commentaries, Economics, Policy, Topology | No Comments »
Saturday, April 30th, 2011 by kc
I recently remotely attended my second meeting of the FCC’s Technological Advisory Council (slides but no video archives). The chairs of four working groups created at the first TAC meeting (Critical Transitions; IPv6; Broadband Infrastructure Deployment; and Sharing Opportunities) presented their interim results. The FCC then issued a set of “TAC recommendations” (which the TAC never saw); it is mostly a wish list from industry to the FCC. Ironically, IPv6 did not appear anywhere in the recommendations, despite being the most popular topic at the first TAC meeting last November, and despite us running out of IPv4 addresses since the last TAC meeting. But the TAC’s IPv6 WG did commit to (on slide 53) delivering a report by November 2011 on what the FCC could or should do to help promote IPv6 deployment. Specifically, the WG has the following charter:
(more…)
Posted in Commentaries, International Networking, IPv6, Policy, Review | No Comments »



