Spoofer Surpasses One Million Sessions and Publishes Final Report
October 13th, 2020 by Josh PolterockOn October 10, 2020 the Spoofer system logged its 1,000,000th measurement session. Finishing its 7th year under CAIDA stewardship, the project recently published its final report documenting the improvements to the software and hardware infrastructure made possible by support from the two-year DHS award “ASPIRE – Augment Spoofer Project to Improve Remediation Efforts” co-led by Matthew Luckie of the University of Waikato’s faculty of Computing and Mathematical Sciences. The report describes (1) updates to the open source client-server source address validation (SAV) testing system (developed under DHS S&T contract D15PC00188) to expand visibility of networks behind Network Address Translation devices (NATs); (2) expanded notifications and reporting through our operator-focused private reporting engine and public regionally-focused notifications to operational mailing lists; (3) several publications documenting analysis of the effectiveness of different approaches to stimulating remediation activities [1, 2, 3]. These tasks achieved testing and evaluation of work developed under the previous contract, and analysis of options for technology transition to a broader cross-section of security research, operations, risk management, and public policy stakeholders. The resulting technologies and data improved the U.S. government’s ability to identify, monitor, and mitigate the infrastructure vulnerability that serves as the primary vector of massive DDoS attacks on the Internet.
Excerpted from the ASPIRE final report:
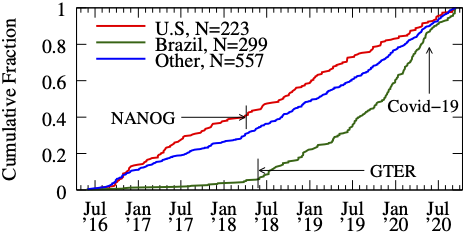
Of the 587 remediation events we inferred between May 2016 and August 2019, 25.2% occurred in the U.S., and 23.5% occurred in Brazil. Figure 8 shows that nearly 90% of the remediation events in Brazil occurred after we began sending monthly emails to the Brazilian operator email list (GTER). We calculate the remediation rate by dividing the number of ASes for which we inferred a remediation event by the total number of ASes that sent a spoofed packet during the same interval. For the year prior to commencing the GTER emails to Brazilian network operators, 14 of 67 ASes (21%) remediated; in the year after, 52 of 168 ASes (31%) remediated. This improvement is supported by NIC.br’s “Program for a Safer Internet” [37], which offers training courses and lectures to support network operators to deploy security best practices in Brazil. The rate of remediation in the U.S. is lower; prior to sending the NANOG emails to U.S. network operators, 21 of 132 (16%) of ASes remediated; in the year after, 35 of 147 (24%) of ASes remediated. While the rate of remediation is lower in the U.S. than Brazil, the relative improvement in both is equivalent –≈50%. Note that remediation in Brazil has slowed since the outbreak of Covid-19 in Brazil.
Figure 8: Remediation in the U.S. and Brazil.
We hope you will take the time to read the full final report, download the client software and test your network to help us better understand the state of IP spoofing.
References:
1. M. Luckie, R. Beverly, R. Koga, K. Keys, J. Kroll, and k. claffy, “Network Hygiene, Incentives, and Regulation: Deployment of Source Address Validation in the Internet”, in ACM Computer and Communications Security (CCS), Nov 2019.
2. L. Müller, M. Luckie, B. Huffaker, k. claffy, and M. Barcellos, “Challenges in Inferring Spoofed Traffic at IXPs”, in ACM SIGCOMM Conference on emerging Networking EXperiments and Technologies (CoNEXT), Dec 2019.
3. L. Müller, M. Luckie, B. Huffaker, k. claffy, and M. Barcellos, “Spoofed traffic inference at IXPs: Challenges, methods and analysis”, Computer Networks, vol. 182, Aug 2020.