Packet Loss Metrics from Darknet Traffic
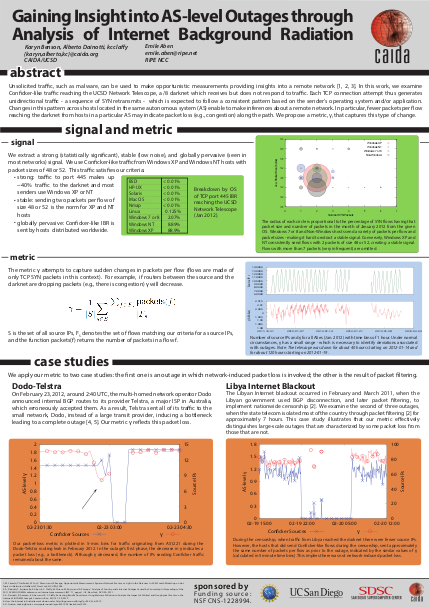
January 17th, 2013 by Karyn BensonAt the CoNEXT Student Workshop, in Nice, France on December 10, 2012, CAIDA shared recent research on Internet outages in a poster entitled “Gaining Insight Into AS-Level Outages through Analysis of Internet Background Radiation.”
An initial task of our NSF-funded DALS SaTC project is to refine and extend indicators to support real-time detection and rapid characterization of Internet connectivity outage events. We used several darknet-based metrics in our studies of country-wide censorship and the impact of political and geophysical events. This latest metric characterizes the number of TCP SYN packets sent from selected networks to the UCSD Network Telescope, to help determine whether packet loss (e.g., because of congestion) is associated with the outage. Since the UCSD Network Telescope receives traffic sent to unassigned IP addresses but does not respond, TCP connection attempts are comprised of only SYN packets. Conficker-like packets comprise the vast majority of these packets, known as Internet Background Radiation. Conficker-infected hosts are known to send two SYN packets per connection attempt, a consistent behavior that allows us to infer packet loss when the number of packets per connection attempt decreases for this type of traffic.
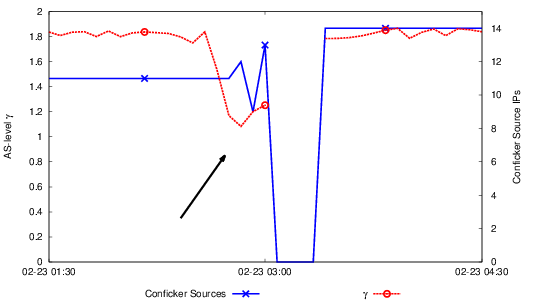
The poster highlights two case studies. In the “Dodo-Telstra” Routing Leakage, caused by a BGP leak, the metric γ decreases significantly, consistent with a bottleneck preceding the outage.
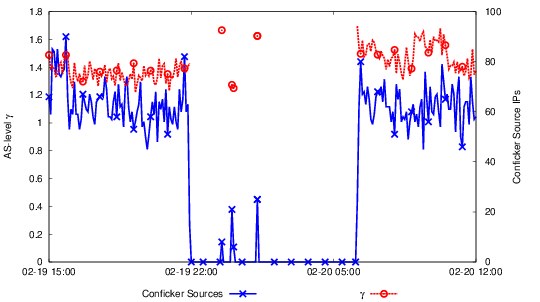
However, during the Libyan Internet Blackout of 2011, where the Libyan government used packet filtering to implement country wide censorship, the value of γ did not change when a few hosts were allowed through the “firewall”. This behavior is consistent with filtering decreasing the number of sources sending traffic without changing its per-flow characteristics.
Our poster was voted as one of the top 8 of the student workshop; these 8 were presented at the main CoNEXT conference.